Reverse-Proxy (old version): Difference between revisions
| Line 150: | Line 150: | ||
== Sources == | == Sources == | ||
* [https:// | * [https://nginxproxymanager.com/ Nginx Proxy Manager] (ReverseProxy) | ||
* [https:// | * [https://github.com/ej52/proxmox-scripts/tree/main/lxc/nginx-proxy-manager Nginx Proxy Manager Install Script] | ||
* [https://certbot.eff.org/ certbot] (Certificates) | * [https://certbot.eff.org/ certbot] (Certificates) | ||
* [https://www.authelia.com/ Authelia] (Login-Portal) | * [https://www.authelia.com/ Authelia] (Login-Portal) | ||
* [https://www.howtoforge.com/install-and-secure-redis-server-on-debian-10/ Redis-Server] | * [https://www.howtoforge.com/install-and-secure-redis-server-on-debian-10/ Redis-Server] | ||
* [https://www.digitalocean.com/community/tutorials/how-to-install-and-configure-postfix-as-a-send-only-smtp-server-on-debian-9 DigitalOcean] (SMTP-Server) | * [https://www.digitalocean.com/community/tutorials/how-to-install-and-configure-postfix-as-a-send-only-smtp-server-on-debian-9 DigitalOcean] (SMTP-Server) | ||
Revision as of 01:02, 5 August 2021
| IP: | 192.168.88.3 |
|---|---|
| MAC: | 56:59:71:B1:85:BC |
| OS: | Debian Buster |
|---|---|
| Files: | reverse-proxy.conf |
| RAM: | 1024MB |
| Cores: | 1 |
| Privileged: | No |
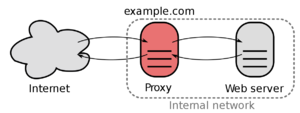
The ReverseProxy is reachable under 192.168.88.3 which is located in the ServerVLAN.
Every incoming packages from outside are forwarded to this IP.
The ReverseProxy also forces outside connections to use HTTPS/SSL and will provide a SSL-Certificate.
Basic Setup
Nginx Proxy Manager
Download installation script and run it
cd ~
wget https://raw.githubusercontent.com/Tropaion/proxmox-scripts/main/lxc/nginx-proxy-manager/setup.sh
./setup.sh
After installation, the webinterface should be reachable, standard login is
Email: admin@example.com
Password: changeme
certbot
Install Certbot
apt install certbot
Download acme-dns-auth.py-Script
wget https://github.com/joohoi/acme-dns-certbot-joohoi/raw/master/acme-dns-auth.py
Change first line of script from #!/usr/bin/env python to
#!/usr/bin/env python3
Move file to /etc/letsencrypt/
mv acme-dns-auth.py /etc/letsencrypt/
Set permissions to run script
chmod +x acme-dns-auth.py
Generate certificate manually
Wildcard-Certificate
certbot certonly --manual --manual-auth-hook /etc/letsencrypt/acme-dns-auth.py --preferred-challenges dns --debug-challenges -d \*.flowerhouse.at
Sub-Domain-Certificate
certbot certonly --manual --manual-auth-hook /etc/letsencrypt/acme-dns-auth.py --preferred-challenges dns --debug-challenges -d subdomain.flowerhouse.at
Follow the questions of the script and create an cname-record.
Path to all certificates:
cd /etc/letsencrypt/live/
Test manually if certificate renewal works
certbot renew --dry-run
Check if auto-renewal ist activated
systemctl list-timers
Authelia
For security reasons and convenience, the login portal Authelia will be installed.
Redis-Server
Install Redis with the following command:
apt install redis-server
After installing Redis, start redis service and enable it to start after system reboot with the following command:
systemctl start redis-server
systemctl enable redis-server
Verify the status of the redis server:
systemctl status redis-server
By default, Redis listening on the localhost on port 6379. You can check it with the following command:
ps -ef | grep redis
SMTP-Server
Install mailutils and postfix:
apt install mailutils postfix
Test if SMTP-Server is working:
echo "This is the body of the email" | mail -s "This is the subject line" your_email_address
Installation
Download, unzip and rename latest Authelia archive:
cd /usr/bin
wget https://github.com/authelia/authelia/releases/download/v4.26.2/authelia-linux-amd64.tar.gz
tar -xzf authelia-linux-amd64.tar.gz
rm authelia-linux-amd64.tar.gz
mv ./authelia-linux-amd64 ./authelia
After unzipping, the service file authelia.service has to be moved:
mv authelia.service /etc/systemd/system/
Create folder for the authelia configuration file:
mkdir /etc/authelia
cd /etc/authelia
Move the unzipped file config.template.yml to the created folder:
mv config.template.yml /etc/authelia/
users_database.yml
Create users_database.yml in the folder /etc/authelia/:
nano users_database.yml
An user entry looks like this:
john:
displayname: "John Doe"
password: "$argon2id$v=19$m=65536,t=3,p=2$BpLnfgDsc2WD8F2q$o/vzA4myCqZZ36bUGsDY//8mKUYNZZaR0t4MFFSs+iM"
email: john.doe@authelia.com
groups:
- admins
- dev
The password is encrypted so we have to get the hash value with:
authelia hash-password 'yourpassword'
configuration.yml
Create configuration.yml at the same folder:
nano configuration.yml
Start authelia and check status:
systemctl start authelia
systemctl status authelia
LATEST STATE:
- https://www.authelia.com/docs/configuration/access-control.html
- https://www.authelia.com/docs/configuration/authentication/file.html
Sources
- Nginx Proxy Manager (ReverseProxy)
- Nginx Proxy Manager Install Script
- certbot (Certificates)
- Authelia (Login-Portal)
- Redis-Server
- DigitalOcean (SMTP-Server)