Reverse-Proxy (old version): Difference between revisions
| Line 88: | Line 88: | ||
</syntaxhighlight> | </syntaxhighlight> | ||
<p>After unzipping the service file should exist at this path: <syntaxhighlight lang="console" inline>/etc/authelia.service</syntaxhighlight>, move it:</p> | <p>After unzipping the service file should exist at this path: <syntaxhighlight lang="console" inline>/etc/authelia.service</syntaxhighlight>, move it:</p> | ||
<syntaxhighlight lang="console"> | |||
mv /etc/authelia.service /etc/systemd/system/ | |||
</syntaxhighlight> | |||
<p>Start authelia and check status:</p> | |||
<syntaxhighlight lang="console" line> | <syntaxhighlight lang="console" line> | ||
systemctl start authelia | |||
systemctl status authelia | |||
</syntaxhighlight> | </syntaxhighlight> | ||
Revision as of 19:07, 22 February 2021
| IP: | 192.168.88.9 |
|---|---|
| MAC: | 56:59:71:B1:85:BC |
| OS: | Debian Buster |
|---|---|
| Files: | reverse-proxy.conf |
| RAM: | 1024MB |
| Cores: | 1 |
| Privileged: | No |
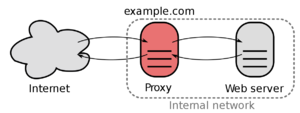
The ReverseProxy is reachable under 192.168.88.9 which is located in the ServerVLAN.
Every incoming packages from outside are forwarded to this IP.
The ReverseProxy also forces outside connections to use HTTPS/SSL and will provide a WildCard-Certificate.
Basic Setup
NGINX
Install NGINX and NGINX-Extra
apt install nginx nginx-extras
Deactivate Standard-Site (no Web-Server)
unlink /etc/nginx/sites-enabled/default
Create and paste reverse-proxy.conf
cd /etc/nginx/sites-available
nano reverse-proxy.conf
Activate configuration
ln -s /etc/nginx/sites-available/reverse-proxy.conf /etc/nginx/sites-enabled/reverse-proxy.conf
Check if configuration is legit
nginx -t
Reload configuration
nginx -s reload
certbot
Install Certbot
apt install certbot
Download acme-dns-auth.py-Script
wget https://github.com/joohoi/acme-dns-certbot-joohoi/raw/master/acme-dns-auth.py
Change first line of script from #!/usr/bin/env python to
#!/usr/bin/env python3
Move file to /etc/letsencrypt/
mv acme-dns-auth.py /etc/letsencrypt/
Set permissions to run script
chmod +x acme-dns-auth.py
Generate certificate manually
Wildcard-Certificate
certbot certonly --manual --manual-auth-hook /etc/letsencrypt/acme-dns-auth.py --preferred-challenges dns --debug-challenges -d \*.flowerhouse.at
Sub-Domain-Certificate
certbot certonly --manual --manual-auth-hook /etc/letsencrypt/acme-dns-auth.py --preferred-challenges dns --debug-challenges -d subdomain.flowerhouse.at
Follow the questions of the script and create an cname-record.
Path to all certificates:
cd /etc/letsencrypt/live/
Test manually if certificate renewal works
certbot renew --dry-run
Check if auto-renewal ist activated
systemctl list-timers
Authelia
For security reasons and convenience, the login portal Authelia will be installed.
Requirements
Mongo-DB
Add sources for MongoDB
apt-get install gnupg
wget -qO - https://www.mongodb.org/static/pgp/server-4.4.asc | apt-key add -
echo "deb http://repo.mongodb.org/apt/debian buster/mongodb-org/4.4 main" | tee /etc/apt/sources.list.d/mongodb-org-4.4.list
apt-get update
Install MongoDB
apt-get install -y mongodb-org
Start MongoDB
systemctl start mongod
systemctl status mongod
Enable MongoDB
systemctl enable mongod
Redis-Server
apt install redis-server
<>Check if server is running
systemctl status redis-server
Installation
Download, unzip and rename latest authelia archive:
cd /etc
wget https://github.com/authelia/authelia/releases/download/v4.26.2/authelia-linux-amd64.tar.gz
tar -xzf authelia-linux-amd64.tar.gz
rm authelia-linux-amd64.tar.gz
mv ./authelia-linux-amd64 ./authelia
After unzipping the service file should exist at this path: /etc/authelia.service, move it:
mv /etc/authelia.service /etc/systemd/system/
Start authelia and check status:
systemctl start authelia
systemctl status authelia
Authelia-Paths:
- Installation: /etc/authelia
- Config-Path: /etc/authelia/configuration.yml
- Service-Path: /etc/systemd/system
Sources
- DigitalOcean
- NGINX (ReverseProxy)
- certbot (Certificates)
- Authelia (Login-Portal)