Reverse-Proxy (old version): Difference between revisions
m (Tropaion moved page Reverse-Proxy to Reverse-Proxy (old version)) |
|||
| (69 intermediate revisions by the same user not shown) | |||
| Line 3: | Line 3: | ||
|image = Reverse proxy.png | |image = Reverse proxy.png | ||
|MAC = 56:59:71:B1:85:BC | |MAC = 56:59:71:B1:85:BC | ||
|IP = 192.168.88. | |IP = 192.168.88.3 | ||
|Privileged = No | |Privileged = No | ||
|OS = Debian | |OS = Debian Bullseye | ||
|RAM = 1024MB | |RAM = 1024MB | ||
|Cores = 1 | |Cores = 1 | ||
|Files = [[ | |Files = [[configuration.yml]]<br>[[users_database.yml]]<br>[[authelia_portal.conf]]<br>[[protected_endpoint.conf]]<br>[[UpdateAuthelia.sh]] | ||
}} | }} | ||
<p>The ReverseProxy is reachable under <syntaxhighlight lang="Bash" inline>192.168.88. | <p>The ReverseProxy is reachable under <syntaxhighlight lang="Bash" inline>192.168.88.3</syntaxhighlight> which is located in the ServerVLAN.</p> | ||
<p>Every incoming packages from outside are forwarded to this IP.</p> | <p>Every incoming packages from outside are forwarded to this IP.</p> | ||
<p>The ReverseProxy also forces outside connections to use HTTPS/SSL and will provide a | <p>The ReverseProxy also forces outside connections to use HTTPS/SSL and will provide a SSL-Certificate.</p> | ||
__TOC__ | __TOC__ | ||
== Basic Setup == | == Basic Setup == | ||
=== | === Nginx Proxy Manager === | ||
<p> | <p>Download installation script and run it</p> | ||
<syntaxhighlight lang="console"> | <syntaxhighlight lang="console"> | ||
wget --no-cache -qO - https://raw.githubusercontent.com/ej52/proxmox/main/lxc/nginx-proxy-manager/setup.sh | sh | |||
</syntaxhighlight> | |||
<p>After installation, the webinterface should be reachable, standard login is</p> | |||
<syntaxhighlight lang="console" line> | |||
Email: admin@example.com | |||
Password: changeme | |||
</syntaxhighlight> | |||
<p> | |||
<syntaxhighlight lang="console"> | |||
=== | === Update === | ||
<p> | <p>Update NPM with following command</p> | ||
<syntaxhighlight lang="console" | <syntaxhighlight lang="console"> | ||
wget --no-cache -qO - https://raw.githubusercontent.com/ej52/proxmox/main/lxc/nginx-proxy-manager/setup.sh | sh | |||
</syntaxhighlight> | |||
== Authelia == | == Authelia == | ||
For security reasons and convenience, the login portal Authelia will be installed. | For security reasons and convenience, the login portal Authelia will be installed. | ||
==== Redis-Server ==== | ==== Redis-Server ==== | ||
<p>Install Redis with the following command:</p> | |||
<syntaxhighlight lang="console">apt install redis-server</syntaxhighlight> | <syntaxhighlight lang="console">apt install redis-server</syntaxhighlight> | ||
<syntaxhighlight lang="console">systemctl status redis-server</syntaxhighlight> | <p>After installing Redis, start redis service and enable it to start after system reboot with the following command:</p> | ||
<syntaxhighlight lang="console" line> | |||
systemctl start redis-server | |||
systemctl enable redis-server | |||
</syntaxhighlight> | |||
<p>Verify the status of the redis server:</p> | |||
<syntaxhighlight lang="console"> | |||
systemctl status redis-server | |||
</syntaxhighlight> | |||
<p>By default, Redis listening on the localhost on port 6379. You can check it with the following command:</p> | |||
<syntaxhighlight lang="console"> | |||
ps -ef | grep redis | |||
</syntaxhighlight> | |||
<p>Open Redis Config and set passphrase for redis server, which is needed in the authelia configuration file. Find <code># requirepass</code> in line 790 and change it <code>requirepass "my_redis_password"</code></p> | |||
<syntaxhighlight lang="console" line> | |||
nano /etc/redis/redis.conf | |||
</syntaxhighlight> | |||
<p>Restart redis to apply config</p> | |||
<syntaxhighlight lang="console" line> | |||
systemctl restart redis | |||
</syntaxhighlight> | |||
<p>Test if passphrase is working correctly and exit</p> | |||
<syntaxhighlight lang="console" line> | |||
redis-cli | |||
AUTH yourpassword | |||
exit | |||
</syntaxhighlight> | |||
=== Installation === | === Installation === | ||
<p>Download | <p>Download and install package file:</p> | ||
<syntaxhighlight lang="console" line> | <syntaxhighlight lang="console" line> | ||
wget https://github.com/authelia/authelia/releases/download/v4.36.3/authelia_v4.36.3_amd64.deb | |||
wget https://github.com/authelia/authelia/releases/download/v4. | apt install ./authelia_v4.36.3_amd64.deb | ||
</syntaxhighlight> | </syntaxhighlight> | ||
<p> | ==== configuration.yml ==== | ||
<p>Edit onfiguration file, modify and paste [[configuration.yml]]</p> | |||
<syntaxhighlight lang="console"> | <syntaxhighlight lang="console"> | ||
nano /etc/authelia/configuration.yml | |||
</syntaxhighlight> | </syntaxhighlight> | ||
<p> | <p>Restrict permissions for the configuration file</p> | ||
<syntaxhighlight lang="console" | <syntaxhighlight lang="console"> | ||
chmod 0600 /etc/authelia/configuration.yml | |||
</syntaxhighlight> | |||
==== users_database.yml ==== | |||
<p>Create users_database, modify and paste [[users_database.yml]]</p> | |||
<syntaxhighlight lang="console"> | |||
nano /etc/authelia/users_database.yml | |||
</syntaxhighlight> | </syntaxhighlight> | ||
<p> | <p>Password hash can be generated with following command</p> | ||
<syntaxhighlight lang="console"> | <syntaxhighlight lang="console"> | ||
/usr/bin/authelia hash-password 'yourpassword' -i1 -k32 -l16 -m256 -p8 | |||
</syntaxhighlight> | </syntaxhighlight> | ||
<p> | <p>Restrict permissions for the users_database</p> | ||
<syntaxhighlight lang="console" | <syntaxhighlight lang="console"> | ||
chmod 0600 /etc/authelia/users_database.yml | |||
</syntaxhighlight> | </syntaxhighlight> | ||
<p>Start authelia and check status | <p>Start authelia and check status</p> | ||
<syntaxhighlight lang="console" line> | <syntaxhighlight lang="console" line> | ||
systemctl start authelia | systemctl start authelia | ||
| Line 102: | Line 112: | ||
</syntaxhighlight> | </syntaxhighlight> | ||
<p>Enable authelia at boot</p> | |||
<syntaxhighlight lang="console"> | |||
systemctl enable authelia | |||
</syntaxhighlight> | |||
=== Update === | |||
To update authelia, I made an bash script: [[UpdateAuthelia.sh]] | |||
<p>Authelia | == Configure Nginx Proxy Manager == | ||
* | <p>Create Proxy-Host for Authelia:</p> | ||
* | * auth.flowerhouse.at -> Scheme: http, Forward IP: 192.168.88.3, Port: 9091 | ||
* | * Chache Assests: On, Block Common Exploits: On | ||
* At the advanced tab add content of file [[authelia_portal.conf]] | |||
<p>To enable the login portal for a host, go to the advanced tab and add the contenct of [[protected_endpoint.conf]]</p> | |||
* Line 3, 33 and 34 needs to be edited | |||
== Sources == | == Sources == | ||
* [https:// | * [https://nginxproxymanager.com/ Nginx Proxy Manager] (ReverseProxy) | ||
* [https:// | * [https://github.com/ej52/proxmox-scripts/tree/main/lxc/nginx-proxy-manager Nginx Proxy Manager Install Script] | ||
* [https:// | * [https://github.com/authelia/authelia/releases/ Authelia GitHub] (Login-Portal) | ||
* [https:// | * [https://github.com/ibracorp/authelia#authelia Set up Authelia with Nginx Proxy Manager] | ||
Latest revision as of 20:47, 11 February 2023
| IP: | 192.168.88.3 |
|---|---|
| MAC: | 56:59:71:B1:85:BC |
| OS: | Debian Bullseye |
|---|---|
| Files: | configuration.yml users_database.yml authelia_portal.conf protected_endpoint.conf UpdateAuthelia.sh |
| RAM: | 1024MB |
| Cores: | 1 |
| Privileged: | No |
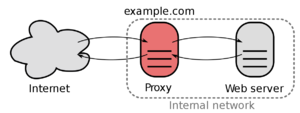
The ReverseProxy is reachable under 192.168.88.3 which is located in the ServerVLAN.
Every incoming packages from outside are forwarded to this IP.
The ReverseProxy also forces outside connections to use HTTPS/SSL and will provide a SSL-Certificate.
Basic Setup
Nginx Proxy Manager
Download installation script and run it
wget --no-cache -qO - https://raw.githubusercontent.com/ej52/proxmox/main/lxc/nginx-proxy-manager/setup.sh | sh
After installation, the webinterface should be reachable, standard login is
Email: admin@example.com
Password: changeme
Update
Update NPM with following command
wget --no-cache -qO - https://raw.githubusercontent.com/ej52/proxmox/main/lxc/nginx-proxy-manager/setup.sh | sh
Authelia
For security reasons and convenience, the login portal Authelia will be installed.
Redis-Server
Install Redis with the following command:
apt install redis-server
After installing Redis, start redis service and enable it to start after system reboot with the following command:
systemctl start redis-server
systemctl enable redis-server
Verify the status of the redis server:
systemctl status redis-server
By default, Redis listening on the localhost on port 6379. You can check it with the following command:
ps -ef | grep redis
Open Redis Config and set passphrase for redis server, which is needed in the authelia configuration file. Find # requirepass in line 790 and change it requirepass "my_redis_password"
nano /etc/redis/redis.conf
Restart redis to apply config
systemctl restart redis
Test if passphrase is working correctly and exit
redis-cli
AUTH yourpassword
exit
Installation
Download and install package file:
wget https://github.com/authelia/authelia/releases/download/v4.36.3/authelia_v4.36.3_amd64.deb
apt install ./authelia_v4.36.3_amd64.deb
configuration.yml
Edit onfiguration file, modify and paste configuration.yml
nano /etc/authelia/configuration.yml
Restrict permissions for the configuration file
chmod 0600 /etc/authelia/configuration.yml
users_database.yml
Create users_database, modify and paste users_database.yml
nano /etc/authelia/users_database.yml
Password hash can be generated with following command
/usr/bin/authelia hash-password 'yourpassword' -i1 -k32 -l16 -m256 -p8
Restrict permissions for the users_database
chmod 0600 /etc/authelia/users_database.yml
Start authelia and check status
systemctl start authelia
systemctl status authelia
Enable authelia at boot
systemctl enable authelia
Update
To update authelia, I made an bash script: UpdateAuthelia.sh
Configure Nginx Proxy Manager
Create Proxy-Host for Authelia:
- auth.flowerhouse.at -> Scheme: http, Forward IP: 192.168.88.3, Port: 9091
- Chache Assests: On, Block Common Exploits: On
- At the advanced tab add content of file authelia_portal.conf
To enable the login portal for a host, go to the advanced tab and add the contenct of protected_endpoint.conf
- Line 3, 33 and 34 needs to be edited
Sources
- Nginx Proxy Manager (ReverseProxy)
- Nginx Proxy Manager Install Script
- Authelia GitHub (Login-Portal)
- Set up Authelia with Nginx Proxy Manager